Oracle Solutions
Dec 23, 2024
Unlocking the Power of Autonomous Database on OCI
The Autonomous Database on Oracle Cloud Infrastructure (OCI) is revolutionising how businesses manage their data, offering unprecedented automation, scalability, and…
Oracle Solutions
Published on May 16, 2024

In cloud computing, businesses are constantly seeking ways to capitalise on its vast potential while ensuring the security of their data and applications. Enter Oracle Cloud Infrastructure (OCI), a platform that not only embraces the possibilities of cloud migration but also addresses the paramount concerns surrounding security.
Yotta, a trusted provider of Oracle solutions and managed services, offers businesses a pathway to maximising the potential of Oracle technologies. By consolidating essential components such as software, licenses, infrastructure, and deployment services, Yotta simplifies operations and drives transformative results across sectors
Yotta: Empowering Businesses with Oracle Solutions and Managed Services
Yotta enables businesses to unlock the full potential of Oracle with its holistic suite of solutions and managed services. Yotta brings everything you need under one roof, from software and licenses to infrastructure and deployment. This unified approach streamlines operations and delivers transformative results across your business.
Yotta’s solutions are designed to scale and adapt to your future needs, ensuring a smooth journey with simplified deployment. A dedicated team of technical, database, and application experts provides ongoing support, so you can focus on core business activities. All this is delivered on a robust, SLA-backed infrastructure that guarantees peak performance.
In addition to its cloud offerings, Yotta’s Oracle Migration Services ensure seamless data migration between on-premise data centers and various cloud environments, minimising the impact on business processes. Yotta provides cross-platform migration services for large databases, leveraging diverse Oracle native tools.
Exploring Security Features of Oracle Cloud Infrastructure
OCI offers a comprehensive set of features designed to protect data. Let’s explore these features in detail:
Encryption at Rest and in Transit: OCI employs advanced encryption techniques to safeguard data both at rest and in transit. Data stored in OCI’s cloud storage services is encrypted using industry-standard encryption algorithms. Additionally, data transferred between OCI services and external networks is encrypted to prevent interception and tampering, providing end-to-end security for data in motion.
OCI ensures data encryption at rest by default, whether stored in storage services like block, object, or file services, or in Oracle platform solutions like Database platform services or Analytics Cloud Service. Encryption extends to database backups for services like Oracle databases, with Oracle managing encryption keys. Customers can opt to manage their own keys, useful for unique keys across teams/projects and for access control. OCI Vault facilitates key management, allowing customers to create vaults and assign keys to OCI services.
Oracle aims to ensure comprehensive encryption, including data in transit. All control plane data within transit undergoes encryption using Transport Layer Security (TLS) 1.2 or higher alongside X.509 certificates. Moreover, data exchanged between different availability domains and regions is secured through MACsec encryption. MACsec (IEEE 802.1AE) functions at the layer 2 level, employing AES-GCM-128 to provide integrity and confidentiality for data in transit.
Identity and Access Management: OCI’s IAM provides the capability to regulate access to cloud resources. IAM Components consist of resources, users, groups, dynamic groups, network sources, compartments, tenancy, policies, home region, and federation. These elements manage access to Oracle Cloud Infrastructure resources. Policies specify resource access, and tenancy serves as the root compartment for all resources, while federation enables integration with identity providers.
OCI offers IAM capabilities to manage user access and permissions effectively. With IAM, businesses can define granular access controls, assign roles and privileges, and implement multi-factor authentication to verify user identities.
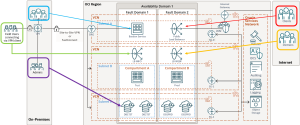
[Image Source: Oracle Blog]
Network Security: The average global cost of a data breach is around $4.45 million. Oracle Cloud Infrastructure prioritises security without compromising cost, offering various protective measures across data center, hardware, network, OS, storage, database, and application access. OCI provides comprehensive network security features to protect against external threats and unauthorised access.
Users accessing OCI from the field face security risks via public networks. To mitigate this, granting access via corporate VPN ensures secure connections. Utilising corporate VPN IP range as a network source allows defining policies for field user access. Virtual Cloud Networks enable businesses to create isolated network environments with customisable security rules, allowing fine-grained control over traffic flow and access to resources. Additionally, OCI offers Distributed Denial of Service (DDoS) protection to mitigate the impact of cyberattacks and ensure the availability of cloud services.
Security Monitoring and Logging: Continuous monitoring and logging are essential components of a robust security strategy, enabling businesses to detect and respond to security incidents in real-time. OCI offers integrated monitoring and logging services that provide visibility into user activities, resource utilisation, and security events. By analysing logs and audit trails, businesses can identify suspicious behavior, investigate security incidents, and enforce compliance with regulatory requirements.
OCI now provides flow logs across all commercial regions, enhancing user experience with granular filtering options. Flow logs aid in monitoring, troubleshooting, and security analysis, offering insights into network behavior. With a simplified interface and configuration controls, they ensure valuable data isn’t lost in the vast network traffic.
Secure Development Practices: OCI follows secure development practices to ensure the integrity and security of its cloud services. By implementing rigorous security testing, code reviews, and vulnerability assessments, OCI mitigates the risk of software vulnerabilities and exploits. Additionally, OCI regularly updates its services with security patches and fixes to address emerging threats and vulnerabilities, ensuring that businesses can rely on a secure and resilient cloud infrastructure.
In conclusion, Oracle Cloud Infrastructure offers a comprehensive suite of security features to protect your cloud environment, ensuring the confidentiality, integrity, and availability of your data and applications. With Yotta’s expertise and industry-leading infrastructure, businesses can harness the full potential of Oracle services while mitigating security risks and optimising costs.

Oracle Solutions
Dec 23, 2024
The Autonomous Database on Oracle Cloud Infrastructure (OCI) is revolutionising how businesses manage their data, offering unprecedented automation, scalability, and…

Oracle Solutions
Nov 14, 2024
Migrating an Oracle Database is a significant process for organisations aiming to modernize infrastructure, improve performance, or transition to the…
Oracle Solutions
Aug 21, 2024
Virtualisation is a cornerstone of modern IT infrastructure, enabling businesses to optimise resources, scale efficiently, and reduce costs. Although VMware…